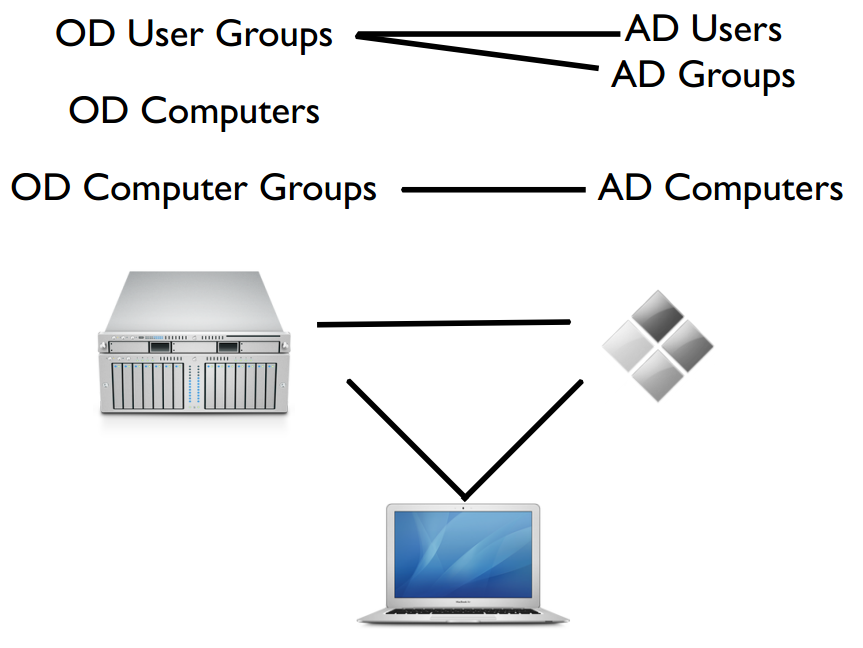
I drove myself crazy reading a lot of people set up their Triangles called Dual Directory, Golden Triangle, Magic Triangle… But you will clearly understand how it all work with this image below from MacSysadmin Magazine.
Clients still use Active Directory for user authentication, while Open Directory supplies Managed Preferences only.
Every Profile Manager instance is an Open Directory Master. Apple has included a local group in Mac OS X Server called Profile Manager ACL. Users and groups from any directory domain that can be viewed in dscl can be added to this group. Adding objects to this group enables them to authenticate to the MyDevices portal but not administrate. Kerberos isn’t really used here, nor are nested groups. You’ll apply policies directly to Active Directory groups in Profile Manager.
Start by enabling directory services debug logging:
odutil set log debug
disable the debug logging:
odutil set log default
Now when you attempt to join Active Directory, you can look at the log at /var/log/opendirectoryd.log to see what’s occurring.
To disable encryption:
/usr/sbin/dsconfigad -packetencrypt disable
To reenable encryption:
/usr/sbin/dsconfigad -packetencrypt allow
When capturing traffic for the following ports:
UDP 53 – DNS
TCP 88 – Kerberos
TCP 389 – LDAP
TCP/UDP 464 – Kerberos Password Changes (KPasswd)
TCP 3268 – Global Catalog (LDAP)
To capture traffic over the built-in Ethernet connection to a file called “capture.out,” you could use the following syntax for tcpdump
tcpdump –K -i en0 -s 0 -w capture.out port 88 or port 464 or port 53 or port 389 or port 3268
Setting Up Profile Manager
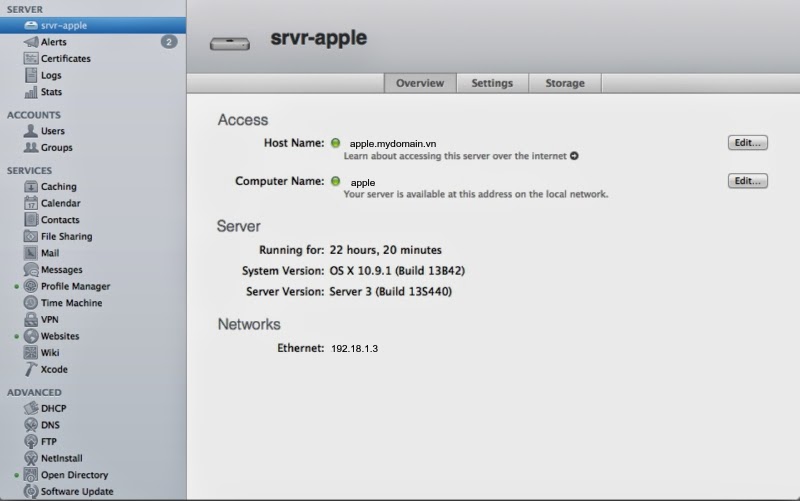
Prepare: HostName, ComputerName, LocalHostName, Static IP, DNS: A, PTR record
apple.mydomain.vn – 192.18.1.3. Go to Server app
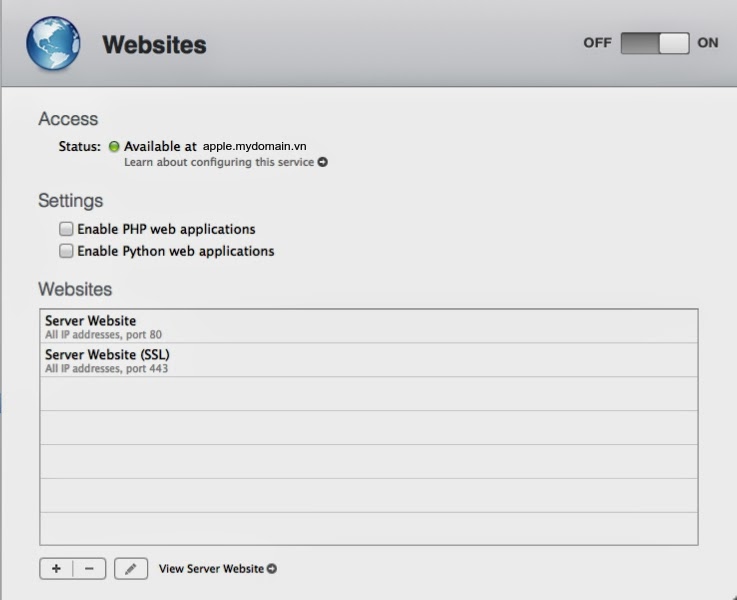
Profile Manager is built on top the web service, APNS and Open Directory
Start the web service (click ON slider) and View Server Website

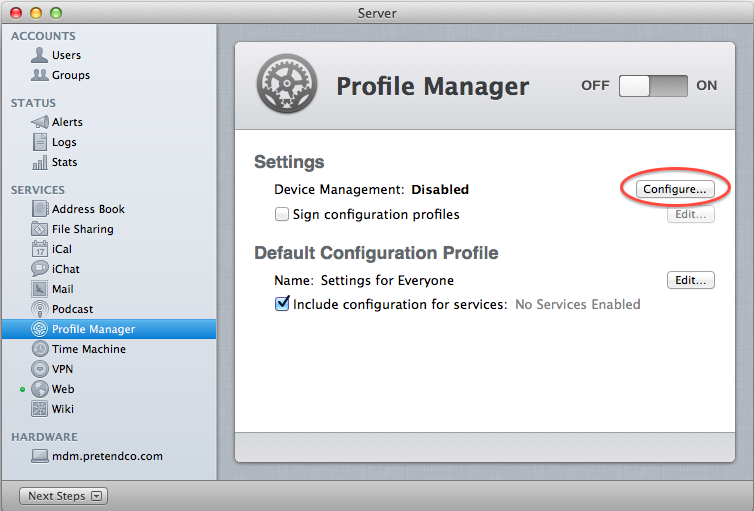
Click on Profile manager service (DO NOT CLICK ON ON/OFF SLIDER)

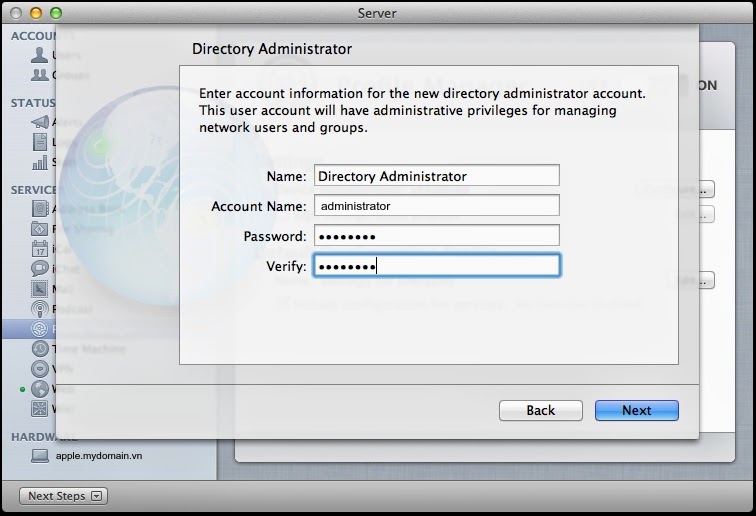
At the Directory Administrator screen, provide the username and password you’d like the Open Directory administrative account to have (note, this is going to be an Open Directory Master

Account Name: administrator
Pass: yourp@ss
The Open Directory master is then created. Even if you’re tying this thing into something like Active Directory, this is going to be a necessary step. Once Open Directory is setup you will be prompted to provide an SSL Certificate.
This can be the certificate provided when Open Directory is initially configured, which is self-signed, or you can select a certificate that you have installed using a CSR from a 3rd party provider.
You will then be prompted to enter the credentials for an Apple Push Notification Service (APNS) certificate. This can be any valid AppleID.
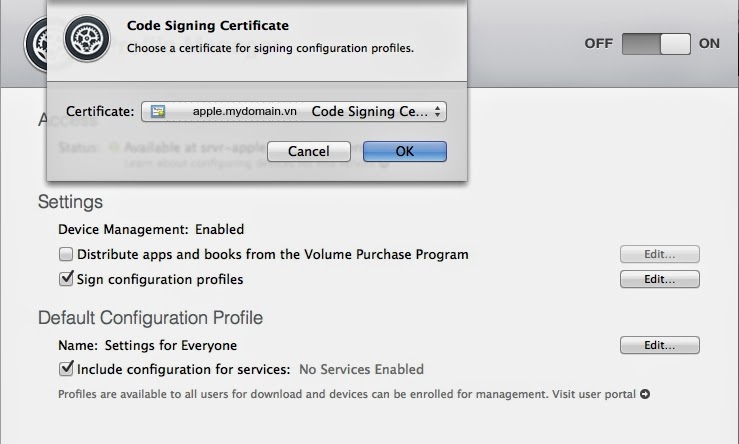
When the assistant closes, you will be back at the Profile Manager screen in the Server application. Here, check the box for Sign Configuration Profiles
=> Import mydomain.vn certificate

Finally Click ON to start Profile Manager -> http://apple.mydomain.vn/profilemanager/
Login with adminitrator yourp@ss
Integrating Mac OS X Lion Server’s Profile Manager With Active Directory
Bind to Active Directory
System Preferences, click on the Users & Groups System Preference pane and click on Login Options. Then click on the Edit… button for the Network Account Server. From here, click on the plus sign (“+”) and enter the domain name into the Server field.
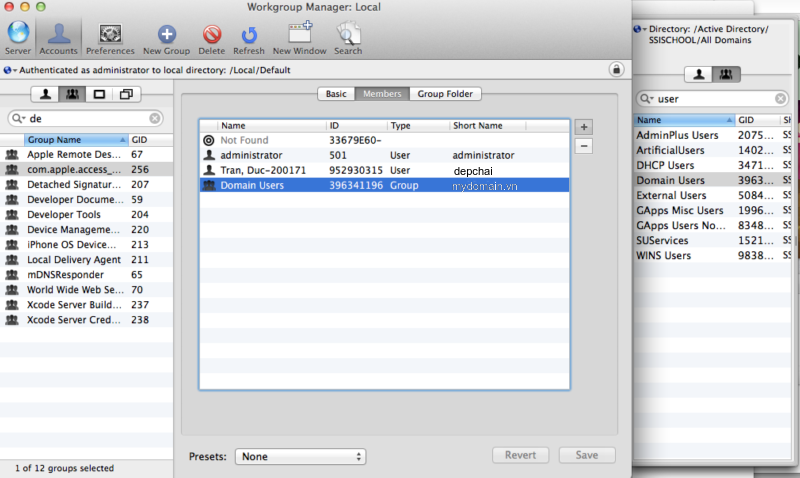
Click on Logout and we’ll fix this. There is no further configuration required for the Active Directory groups to function properly in regards to how they work with the server. However, we will need to open Workgroup Manager and nest some groups. You might think that you’d be doing something all kinds of complicated, but notsomuch. You also might think that you would be nesting the Active Directory users and groups inside Open Directory groups, given that you have to enable Open Directory in order to use Profile Manager. Again, notsomuch. To nest the groups, browse to the local directory and then then click on the com.apple.access_devicemanagement group.
Click on the lock icon to unlock the directory domain, authenticating when prompted.
Click on the Members tab and then click on the plus sign (“+”) to add members to the group. Workgroup manager -> View -> Show system record
Then in the menu that slid out, click on the domain browser at the top of that menu and select the Active Directory entry.

Test Access
Drag the user or group from the menu into the list of members and then click on the Save button.
Now log in again using the MyDevices portal and you’ll be able to Enroll. From within Profile Manager (log in here as a local administrator), you’ll see all of the users and groups and be able to apply policies directly to them by clicking on the Edit button for each (the information isn’t saved in the directory service on the server, but is cached into the directory service client on the client when using Mac OS X 10.7, Lion based clients).
To enroll devices for management, use the URL -> https://apple.mydomain.vn/mydevices/
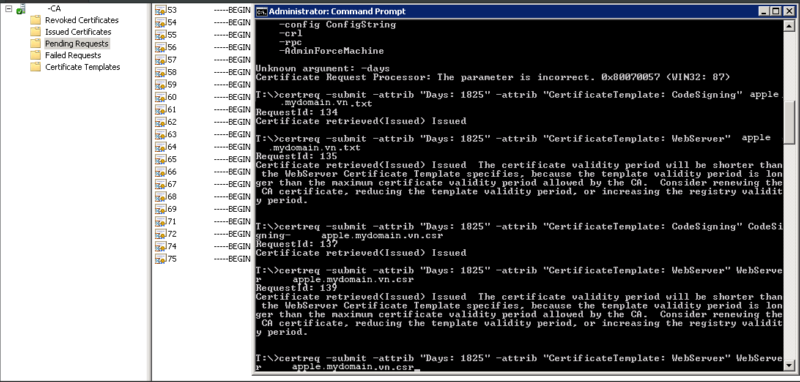
To Sign Certificate -> Create a CSR from Certificate Management from Server.app, then open Certificate Authority on Windows Server 2008 create a Code Signing from Certificate Template -> use command line to sign the CSR file

Reference:
http://krypted.com/iphone/setting-up-profile-manager-in-lion-server/
http://krypted.com/mac-security/integrating-mac-os-x-lion-servers-profile-manager-with-active-directory/